It's always a good practice to restrict files that is not intend for normal users. The easiest way is to not place the file in the web directory.The recommended way is to forbidden file access is to use the System.Web.HttpForbiddenHandler.
By default, ASP.NET is configured to intercept and to stop requests for several different file types that are used in ASP.NET applications and these are configured in the root Web.config.
Here are the file types that are configured by default to be forbidden from user access.
*.asax, *.ascx, *.master, *.skin, *.browser, *.sitemap, *.config, *.cs, *.csproj, *.vb, *.vbproj, *.webinfo, *.licx, *.resx, *.resources, *.mdb, *.vjsproj, *.java, *.jsl, *.ldb, *.dsdgm, *.ssdgm, *.lsad, *.ssmap, *.cd, *.dsprototype, *.lsaprototype, *.sdm, *.sdmDocument, *.mdf, *.ldf
ASP.NET ensures the privacy of these files by associating both file types with System.Web.HttpForbiddenHandler. If the forbidden file is requested, System.Web.HttpForbiddenHandler returns an error to the user as a response to the request.
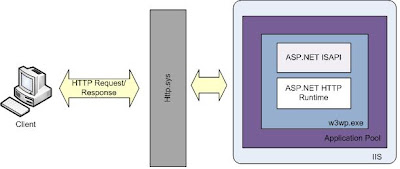
Here is the high level overview of how the page is served
When a request hits the IIS Web server, the file extension is examined and based on its extension the request is handled by IIS itself or it is directed to the ISAPI extension. When it comes to static file like .htm, IIS handles it and returns back the contents of it but in case of dynamic files like .aspx IIS routes the request to the aspnet_isapi.dll ISAPI extension, the ISAPI extension routes the request onto the ASP.NET engine which maps the file extension to HTTP Handlers. For example, ASP.NET Web pages are rendered by the PageHandlerFactory; the SOAP responses of Web services are generated by the WebServiceFactoryHandler. The PageHandlerFactory knows how to render the HTML markup of an ASP.NET Web page; the WebServiceFactoryHandler knows how to accept incoming SOAP requests, invoke the proper Web service method, and return the response in a properly formatted SOAP response.
Protecting the files
In order for ASP.NET to block the desired file type IIS needs to be configured to forward the requests to ASP.NET and also the web.config of the application needs to be configured to block the desired file type.
Configuring IIS to block the desired file type
In the Web.config file add the <httpHandlers> configuration element under the <system.web> element.
By default, ASP.NET is configured to intercept and to stop requests for several different file types that are used in ASP.NET applications and these are configured in the root Web.config.
Here are the file types that are configured by default to be forbidden from user access.
*.asax, *.ascx, *.master, *.skin, *.browser, *.sitemap, *.config, *.cs, *.csproj, *.vb, *.vbproj, *.webinfo, *.licx, *.resx, *.resources, *.mdb, *.vjsproj, *.java, *.jsl, *.ldb, *.dsdgm, *.ssdgm, *.lsad, *.ssmap, *.cd, *.dsprototype, *.lsaprototype, *.sdm, *.sdmDocument, *.mdf, *.ldf
ASP.NET ensures the privacy of these files by associating both file types with System.Web.HttpForbiddenHandler. If the forbidden file is requested, System.Web.HttpForbiddenHandler returns an error to the user as a response to the request.
Here is the high level overview of how the page is served
When a request hits the IIS Web server, the file extension is examined and based on its extension the request is handled by IIS itself or it is directed to the ISAPI extension. When it comes to static file like .htm, IIS handles it and returns back the contents of it but in case of dynamic files like .aspx IIS routes the request to the aspnet_isapi.dll ISAPI extension, the ISAPI extension routes the request onto the ASP.NET engine which maps the file extension to HTTP Handlers. For example, ASP.NET Web pages are rendered by the PageHandlerFactory; the SOAP responses of Web services are generated by the WebServiceFactoryHandler. The PageHandlerFactory knows how to render the HTML markup of an ASP.NET Web page; the WebServiceFactoryHandler knows how to accept incoming SOAP requests, invoke the proper Web service method, and return the response in a properly formatted SOAP response.
Protecting the files
In order for ASP.NET to block the desired file type IIS needs to be configured to forward the requests to ASP.NET and also the web.config of the application needs to be configured to block the desired file type.
Configuring IIS to block the desired file type
- Open IIS and right-click on the web site/virtual directory and choose "Properties"
- Navigate to the Home Directory tab and click "Configuration"
- To add application mappings for each extension that you want ASP.NET to block, click Add. Then, in the Executable field, fill in the path of your aspnet_isapi.dll.
- To identify the location of the Aspnet_isapi.dll file that handles the ASP.NET requests, select the .aspx application mapping and then click Edit.Mostly the ISAPI extension will be at $WINDOWS_DIR$\Microsoft.Net\Framework\$VERSION$
- In the "Extension" Field, Enter the file type. for example, .ini
- In the Verbs section, select the All Verbs option. Verify that the Script Engine check box is selected and that the Check If File Exists check box is not selected.
- Click OK.
- If required, Repeat this procedure for every file name extension that you want to have processed by ASP.NET.
 |
| Web Site Properties |
 |
| Application Configuration |
In the Web.config file add the <httpHandlers> configuration element under the <system.web> element.
The above is for IIS version prior to 7.0. IIS 7.0 supports 2 modes, Integrated and Classic. Integrated is the default mode for ASP.NET apps on IIS 7.0 which require handlers to be placed in <system.webServer>/<handlers> instead of <system.web>/<httpHandlers>. Here is the config for IIS 7.0
Apart from System.Web.HttpForbiddenHandler which issues the HTTP 403 error "Forbidden: Access is denied" when an attempt is made to access a forbidden resource "System.Web.StaticFileHandler" can be used which generates one of the following errors: HTTP 401 error "Unauthorized"; HTTP 403 error "Forbidden: Access is denied"; or HTTP 404 error "File or directory not found".
Happy Coding!!!